先日、インストールしたWindows 10のWindows Subsystem for Linux(WSL)上で動作するKali Linuxにsshが無いので追加しました。
- sshのインストール
- sshクライアント
- sshサーバ
- ローカルでsshサーバに接続
- リモートからsshサーバに接続
- rootのパスワード設定
- ipコマンドがエラー
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
rootlinks@Win10:~$ apt-cache search ssh | grep ^ssh ssh - secure shell client and server (metapackage) ssh-agent-filter - filtering proxy for ssh-agent ssh-askpass - under X, asks user for a passphrase for ssh-add ssh-askpass-fullscreen - Under Gnome2, asks user for a passphrase for ssh-add ssh-askpass-gnome - interactive X program to prompt users for a passphrase for ssh-add ssh-audit - tool for ssh server auditing ssh-contact - establish SSH connections to your IM contacts using Telepathy (metapackage) ssh-contact-client - establish SSH connections to your IM contacts using Telepathy (client) ssh-contact-service - establish SSH connections to your IM contacts using Telepathy (server) ssh-cron - cron daemon allowing ssh keys with passphrases to be used ssh-import-id - securely retrieve an SSH public key and install it locally sshcommand - turn SSH into a thin client specifically for your command sshfp - DNS SSHFP records generator sshfs - filesystem client based on SSH File Transfer Protocol sshguard - Protects from brute force attacks against ssh sshpass - Non-interactive ssh password authentication sshuttle - Transparent proxy server for VPN over SSH rootlinks@Win10:~$ sudo apt-get install -y ssh Reading package lists... Done Building dependency tree Reading state information... Done The following additional packages will be installed: ncurses-term openssh-client openssh-server openssh-sftp-server Suggested packages: keychain libpam-ssh monkeysphere ssh-askpass molly-guard rssh ufw The following NEW packages will be installed: ncurses-term openssh-client openssh-server openssh-sftp-server ssh 0 upgraded, 5 newly installed, 0 to remove and 0 not upgraded. Need to get 1,829 kB of archives. After this operation, 9,722 kB of additional disk space will be used. (snip) |
当たり前ですが、他のサーバに接続できました。
|
1 2 3 4 5 6 7 8 9 10 11 |
rootlinks@Win10:~$ ssh -V OpenSSH_7.6p1 Debian-4, OpenSSL 1.0.2n 7 Dec 2017 rootlinks@Win10:~$ ssh usage: ssh [-46AaCfGgKkMNnqsTtVvXxYy] [-b bind_address] [-c cipher_spec] [-D [bind_address:]port] [-E log_file] [-e escape_char] [-F configfile] [-I pkcs11] [-i identity_file] [-J [user@]host[:port]] [-L address] [-l login_name] [-m mac_spec] [-O ctl_cmd] [-o option] [-p port] [-Q query_option] [-R address] [-S ctl_path] [-W host:port] [-w local_tun[:remote_tun]] [user@]hostname [command] |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 |
rootlinks@Win10:~$ cat /etc/ssh/sshd_config # $OpenBSD: sshd_config,v 1.101 2017/03/14 07:19:07 djm Exp $ # This is the sshd server system-wide configuration file. See # sshd_config(5) for more information. # This sshd was compiled with PATH=/usr/bin:/bin:/usr/sbin:/sbin # The strategy used for options in the default sshd_config shipped with # OpenSSH is to specify options with their default value where # possible, but leave them commented. Uncommented options override the # default value. #Port 22 #AddressFamily any #ListenAddress 0.0.0.0 #ListenAddress :: #HostKey /etc/ssh/ssh_host_rsa_key #HostKey /etc/ssh/ssh_host_ecdsa_key #HostKey /etc/ssh/ssh_host_ed25519_key # Ciphers and keying #RekeyLimit default none # Logging #SyslogFacility AUTH #LogLevel INFO # Authentication: #LoginGraceTime 2m #PermitRootLogin prohibit-password #StrictModes yes #MaxAuthTries 6 #MaxSessions 10 #PubkeyAuthentication yes # Expect .ssh/authorized_keys2 to be disregarded by default in future. #AuthorizedKeysFile .ssh/authorized_keys .ssh/authorized_keys2 #AuthorizedPrincipalsFile none #AuthorizedKeysCommand none #AuthorizedKeysCommandUser nobody # For this to work you will also need host keys in /etc/ssh/ssh_known_hosts #HostbasedAuthentication no # Change to yes if you don't trust ~/.ssh/known_hosts for # HostbasedAuthentication #IgnoreUserKnownHosts no # Don't read the user's ~/.rhosts and ~/.shosts files #IgnoreRhosts yes # To disable tunneled clear text passwords, change to no here! #PasswordAuthentication yes #PermitEmptyPasswords no # Change to yes to enable challenge-response passwords (beware issues with # some PAM modules and threads) ChallengeResponseAuthentication no # Kerberos options #KerberosAuthentication no #KerberosOrLocalPasswd yes #KerberosTicketCleanup yes #KerberosGetAFSToken no # GSSAPI options #GSSAPIAuthentication no #GSSAPICleanupCredentials yes #GSSAPIStrictAcceptorCheck yes #GSSAPIKeyExchange no # Set this to 'yes' to enable PAM authentication, account processing, # and session processing. If this is enabled, PAM authentication will # be allowed through the ChallengeResponseAuthentication and # PasswordAuthentication. Depending on your PAM configuration, # PAM authentication via ChallengeResponseAuthentication may bypass # the setting of "PermitRootLogin without-password". # If you just want the PAM account and session checks to run without # PAM authentication, then enable this but set PasswordAuthentication # and ChallengeResponseAuthentication to 'no'. UsePAM yes #AllowAgentForwarding yes #AllowTcpForwarding yes #GatewayPorts no X11Forwarding yes #X11DisplayOffset 10 #X11UseLocalhost yes #PermitTTY yes PrintMotd no #PrintLastLog yes #TCPKeepAlive yes #UseLogin no #PermitUserEnvironment no #Compression delayed #ClientAliveInterval 0 #ClientAliveCountMax 3 #UseDNS no #PidFile /var/run/sshd.pid #MaxStartups 10:30:100 #PermitTunnel no #ChrootDirectory none #VersionAddendum none # no default banner path #Banner none # Allow client to pass locale environment variables AcceptEnv LANG LC_* # override default of no subsystems Subsystem sftp /usr/lib/openssh/sftp-server # Example of overriding settings on a per-user basis #Match User anoncvs # X11Forwarding no # AllowTcpForwarding no # PermitTTY no # ForceCommand cvs server |
起動してみます。起動にはinitd経由でのスクリプトが用意されています。
|
1 2 3 4 5 6 7 8 9 |
rootlinks@Win10:~$ sudo /etc/init.d/ssh start [ ok ] Starting OpenBSD Secure Shell server: sshd. rootlinks@Win10:~$ ps aux USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND root 1 0.0 0.0 10356 104 ? Ss 10:19 0:00 /init rootlin+ 2 0.0 0.0 24408 1496 tty1 Ss 10:19 0:01 -bash root 1677 0.0 0.0 79292 820 ? Ss 11:16 0:00 /usr/sbin/sshd rootlin+ 1695 0.0 0.0 39720 1884 tty1 R 11:16 0:00 ps aux |
ちなみにsystemd経由ではsystemdが起動されていないのでエラーになります。
|
1 2 3 4 5 6 |
rootlinks@Win10:~$ systemctl list-unit-files --type=service | grep ssh ssh.service disabled ssh@.service static rootlinks@Win10:~$ sudo systemctl start ssh System has not been booted with systemd as init system (PID 1). Can't operate. |
ローカルからsshサーバに接続してみます。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
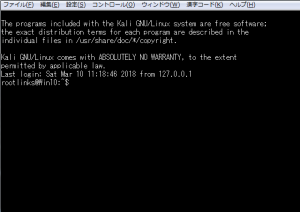
rootlinks@Win10:~$ ssh rootlinks@localhost The authenticity of host 'localhost (127.0.0.1)' can't be established. ECDSA key fingerprint is SHA256:030Sshosdflksjidrklwfsfosadifsadkfjv. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'localhost' (ECDSA) to the list of known hosts. rootlinks@localhost's password: The programs included with the Kali GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Kali GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. rootlinks@Win10:~$ exit logout Connection to localhost closed. |
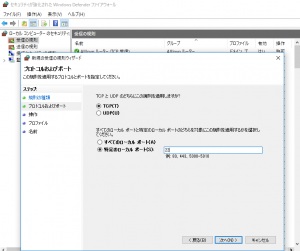
他のWindowsパソコンからKali Linuxにssh接続してみます。
Windows Firewallが有効な場合はポート22への接続を許可するルールを追加して下さい。
デフォルトではrootのパスワードはtoorの設定なのですが、エラーになりました。
Kali Linux Default Passwords
https://docs.kali.org/introduction/kali-linux-default-passwords
どちらにしろ変更は必要なので変更しました。
|
1 2 3 4 5 6 7 8 9 10 |
rootlinks@Win10:~$ su - Password: su: Authentication failure rootlinks@Win10:~$ sudo passwd root Enter new UNIX password: Retype new UNIX password: passwd: password updated successfully rootlinks@Win10:~$ su - Password: root@Win10:~# |
ipコマンドがエラーになります。
|
1 2 3 |
rootlinks@Win10:~$ ip addr DONE truncated Dump terminated |
代わりにifconfigなど使いそうなプログラムをインストールしました。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
rootlinks@Win10:~$ sudo apt-get install -y file curl git net-tools rootlinks@Win10:~$ ifconfig eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.1.1 netmask 255.255.255.0 broadcast 192.168.1.255 inet6 2408:212:d01:b100:103d:4454:549a:596b prefixlen 64 scopeid 0x0<global> inet6 2408:212:d01:b100:257d:4b7:8ac3:8842 prefixlen 128 scopeid 0x0<global> inet6 fe80::103d:4454:549a:596c prefixlen 64 scopeid 0xfd<compat,link,site,host> ether 00:0c:28:bc:0a:54 (Ethernet) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 lo: flags=73<UP,LOOPBACK,RUNNING> mtu 1500 inet 127.0.0.1 netmask 255.0.0.0 inet6 ::1 prefixlen 128 scopeid 0x0<global> loop (Local Loopback) RX packets 0 bytes 0 (0.0 B) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 0 bytes 0 (0.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 |