Windows 10のWindows Subsystem for Linux(WSL)上で動作するKali Linuxにproxychainsをインストールしてみました。
- proxychainsのインストール
- 設定ファイル(/etc/proxychains.conf)
- tor proxyの起動
- 確認
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 |
rootlinks@Win10:~$ apt show proxychains Package: proxychains Version: 3.1-7 Priority: optional Section: net Maintainer: Daniel Echeverry <epsilon77@gmail.com> Installed-Size: 28.7 kB Depends: libproxychains3 (>= 3.1-7) Homepage: http://proxychains.sourceforge.net Tag: implemented-in::c, interface::commandline, network::vpn, role::program, use::proxying Download-Size: 9,188 B APT-Manual-Installed: yes APT-Sources: http://http.kali.org/kali kali-rolling/main amd64 Packages Description: proxy chains - redirect connections through proxy servers Proxy chains force any tcp connection made by any given tcp client to follow through proxy (or proxy chain). It is a kind of proxifier. It acts like sockscap / premeo / eborder driver ( intercepts TCP calls ) . This version supports SOCKS4, SOCKS5 and HTTP CONNECT proxy servers. Different proxy types can be mixed in the same chain. . Features * Access Internet from behind restrictive firewall. * Source IP masquerade. * SSH tunneling and forwarding. * Dynamic LAN-to-LAN VPN channel. * Servers and daemons friendly (works fine with sendmail MTA). . http://proxychains.sourceforge.net rootlinks@Win10:~$ sudo apt -y install proxychains Reading package lists... Done Building dependency tree Reading state information... Done The following package was automatically installed and is no longer required: libpoppler72 (snip) |
デフォルトでtor proxyの設定が記述されています。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 |
rootlinks@Win10:~$ cat /etc/proxychains.conf # proxychains.conf VER 3.1 # # HTTP, SOCKS4, SOCKS5 tunneling proxifier with DNS. # # The option below identifies how the ProxyList is treated. # only one option should be uncommented at time, # otherwise the last appearing option will be accepted # #dynamic_chain # # Dynamic - Each connection will be done via chained proxies # all proxies chained in the order as they appear in the list # at least one proxy must be online to play in chain # (dead proxies are skipped) # otherwise EINTR is returned to the app # strict_chain # # Strict - Each connection will be done via chained proxies # all proxies chained in the order as they appear in the list # all proxies must be online to play in chain # otherwise EINTR is returned to the app # #random_chain # # Random - Each connection will be done via random proxy # (or proxy chain, see chain_len) from the list. # this option is good to test your IDS :) # Make sense only if random_chain #chain_len = 2 # Quiet mode (no output from library) #quiet_mode # Proxy DNS requests - no leak for DNS data proxy_dns # Some timeouts in milliseconds tcp_read_time_out 15000 tcp_connect_time_out 8000 # ProxyList format # type host port [user pass] # (values separated by 'tab' or 'blank') # # # Examples: # # socks5 192.168.67.78 1080 lamer secret # http 192.168.89.3 8080 justu hidden # socks4 192.168.1.49 1080 # http 192.168.39.93 8080 # # # proxy types: http, socks4, socks5 # ( auth types supported: "basic"-http "user/pass"-socks ) # [ProxyList] # add proxy here ... # meanwile # defaults set to "tor" socks4 127.0.0.1 9050 |
下記の記事でtor proxyをインストールしたので起動してみます。
デフォルトはポート9050で起動します。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
rootlinks@Win10:~$ tor & [1] 749 rootlinks@Win10:~$ Mar 20 21:10:48.252 [notice] Tor 0.3.2.10 (git-0edaa32732ec8930) running on Linux with Libevent 2.1.8-stable, OpenSSL 1.1.0g, Zlib 1.2.8, Liblzma 5.2.2, and Libzstd 1.3.3. Mar 20 21:10:48.254 [notice] Tor can't help you if you use it wrong! Learn how to be safe at https://www.torproject.org/download/download#warning Mar 20 21:10:48.256 [notice] Read configuration file "/etc/tor/torrc". Mar 20 21:10:48.260 [notice] Scheduler type KIST has been enabled. Mar 20 21:10:48.260 [notice] Opening Socks listener on 127.0.0.1:9050 Mar 20 21:10:48.000 [notice] Parsing GEOIP IPv4 file /usr/share/tor/geoip. Mar 20 21:10:48.000 [notice] Parsing GEOIP IPv6 file /usr/share/tor/geoip6. Mar 20 21:10:48.000 [notice] Bootstrapped 0%: Starting Mar 20 21:10:48.000 [notice] Starting with guard context "default" Mar 20 21:10:48.000 [notice] Bootstrapped 80%: Connecting to the Tor network Mar 20 21:10:50.000 [notice] Bootstrapped 85%: Finishing handshake with first hopMar 20 21:10:51.000 [notice] Bootstrapped 90%: Establishing a Tor circuit Mar 20 21:10:52.000 [notice] Tor has successfully opened a circuit. Looks like client functionality is working. Mar 20 21:10:52.000 [notice] Bootstrapped 100%: Done rootlinks@Win10:~$ ps PID TTY TIME CMD 2 tty1 00:00:00 bash 749 tty1 00:00:00 tor 750 tty1 00:00:00 ps |
tor proxyのアクセス許可などの設定は/etc/tor/torrcを編集して下さい。
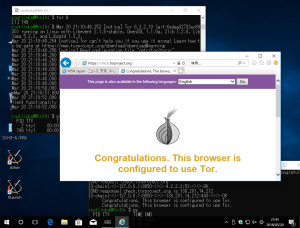
https://check.torproject.org/に接続してtor経由になっているか確認します。
Congratulationsと表示されればtor経由になっています。
|
1 2 3 4 5 6 7 |
rootlinks@Win10:~$ proxychains curl -kLs https://check.torproject.org/ | grep -i congratulations |DNS-request| check.torproject.org |S-chain|-<>-127.0.0.1:9050-<><>-4.2.2.2:53-<><>-OK |DNS-response| check.torproject.org is 138.201.14.212 |S-chain|-<>-127.0.0.1:9050-<><>-138.201.14.212:443-<><>-OK Congratulations. This browser is configured to use Tor. Congratulations. This browser is configured to use Tor. |
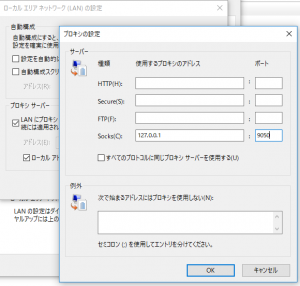
試しにWindows 10のInternet Explorerにtor proxyを設定してみます。
https://check.torproject.orgに接続するとCongratulationsです。
参考
ProxyChains をちょっと便利に使う
https://blog.kteru.net/proxychains-tips/