CentOS 7のFirewallで当然想定される「特定のポートに特定のネットワークから許可」というのを調べてみました。
firewall-cmd --directでも出来そうですがfirewall-cmd --add-rich-ruleの方が個人的には分かりやすいです。
RHEL7: How to get started with Firewalld.
http://www.certdepot.net/rhel7-get-started-firewalld/
firewall-cmd --add-rich-ruleはrich言語でルールを追加する方法です。
※man firewall-cmdから抜粋
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
[--permanent] [--zone=zone] --list-rich-rules List rich language rules added for zone as a newline separated list. If zone is omitted, default zone will be used. [--permanent] [--zone=zone] --add-rich-rule='rule' [--timeout=timeval] Add rich language rule 'rule' for zone. This option can be specified multiple times. If zone is omitted, default zone will be used. If a timeout is supplied, the rule will be active for the specified amount of time and will be removed automatically afterwards. timeval is either a number (of seconds) or number followed by one of characters s (seconds), m (minutes), h (hours), for example 20m or 1h. For the rich language rule syntax, please have a look at firewalld.richlanguage(5). The --timeout option is not combinable with the --permanent option. [--permanent] [--zone=zone] --remove-rich-rule='rule' Remove rich language rule 'rule' from zone. This option can be specified multiple times. If zone is omitted, default zone will be used. For the rich language rule syntax, please have a look at firewalld.richlanguage(5). [--permanent] [--zone=zone] --query-rich-rule='rule' Return whether a rich language rule 'rule' has been added for zone. If zone is omitted, default zone will be used. Returns 0 if true, 1 otherwise. For the rich language rule syntax, please have a look at firewalld.richlanguage(5). |
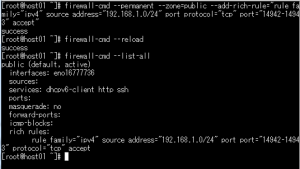
今回はServerProtectの管理ポートhttp(14942),https(14943)をネットワーク192.168.1.0/24からのみ接続を許可します。
- 現状の確認
- rich ruleの追加
- reload
- rich ruleの一覧
- rich ruleの検索
- rich ruleの削除
- reload
|
1 2 3 4 5 6 7 8 9 10 |
[root@host01 ~]# firewall-cmd --list-all public (default, active) interfaces: eno16777736 sources: services: dhcpv6-client http ssh ports: masquerade: no forward-ports: icmp-blocks: rich rules: |
|
1 2 3 4 5 6 7 8 9 10 11 12 |
[root@host01 ~]# firewall-cmd --permanent --zone=public --add-rich-rule="rule family="ipv4" source address="192.168.1.0/24" port protocol="tcp" port="14942-14943" accept" success [root@host01 ~]# firewall-cmd --list-all public (default, active) interfaces: eno16777736 sources: services: dhcpv6-client http ssh ports: masquerade: no forward-ports: icmp-blocks: rich rules: |
再読み込みをして設定を反映させます。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
[root@host01 ~]# firewall-cmd --reload success [root@host01 ~]# firewall-cmd --list-all public (default, active) interfaces: eno16777736 sources: services: dhcpv6-client http ssh ports: masquerade: no forward-ports: icmp-blocks: rich rules: rule family="ipv4" source address="192.168.1.0/24" port port="14942-14943" protocol="tcp" accept |
|
1 2 |
[root@host01 ~]# firewall-cmd --list-rich-rule rule family="ipv4" source address="192.168.1.0/24" port port="14942-14943" protocol="tcp" accept |
shell script等でルールの存在を確認して、無ければ追加するっていうような作業に使うのでしょうか。
・ある場合
|
1 2 |
[root@host01 ~]# firewall-cmd --permanent --zone=public --query-rich-rule="rule family="ipv4" source address="192.168.1.0/24" port protocol="tcp" port="14942-14943" accept" yes |
・ない場合
|
1 2 |
[root@host01 ~]# firewall-cmd --permanent --zone=public --query-rich-rule="rule family="ipv4" source address="192.168.2.0/24" port protocol="tcp" port="14942-14943" accept" no |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
[root@host01 ~]# firewall-cmd --permanent --zone=public --remove-rich-rule="rule family="ipv4" source address="192.168.1.0/24" port protocol="tcp" port="14942-14943" accept" success [root@host01 ~]# firewall-cmd --list-all public (default, active) interfaces: eno16777736 sources: services: dhcpv6-client http ssh ports: masquerade: no forward-ports: icmp-blocks: rich rules: rule family="ipv4" source address="192.168.1.0/24" port port="14942-14943" protocol="tcp" accept |
|
1 2 3 4 5 6 7 8 9 10 11 12 |
[root@host01 ~]# firewall-cmd --reload success [root@host01 ~]# firewall-cmd --list-all public (default, active) interfaces: eno16777736 sources: services: dhcpv6-client http ssh ports: masquerade: no forward-ports: icmp-blocks: rich rules: |
rich ruleが複数あった場合の処理などまだまだ不明な点はありますが、取り敢えず入口に辿り着いた感じです(^^;;
rich languageについてはman firewalld.richlanguageをどうぞ。