以前、Ubuntu 20にCentrify ExpressをインストールしてWindows Active Directory認証でログインできるようにしました。
今回はSystem Security Services Daemon(SSSD)を使用してActive DIrectoryにドメイン参加、認証ができるようにしてみたいと思います。
下記のサイトをそのままやるだけですが(^^;
Service – SSSD | Ubuntu
https://ubuntu.com/server/docs/service-sssd
環境
- Active Directory
- Ubuntu
・Windows Server 2019評価版
・Domain example.jp
・IP: 192.168.1.1
・Ubuntu 20.04.3 LTS DESKTOP
・IP: 192.168.1.2
- Ubuntu Update
- 必要なパッケージのインストール
- DNS設定の確認
- ドメインがDNS経由で検出できるか確認
- ドメイン参加
- SSSDの設定
- ホームディレクトリの自動作成
- 確認
- ADユーザの情報取得
- ユーザguest01のグループ情報
- guest01でログイン
|
1 2 3 |
rootlinks@Ubuntu20:~$ sudo apt update rootlinks@Ubuntu20:~$ sudo apt upgrade |
sssd-ad, sssd-tools, realmd, adcliをインストールします。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 |
rootlinks@Ubuntu20:~$ sudo apt install sssd-ad sssd-tools realmd adcli Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: libfprint-2-tod1 libllvm10 linux-headers-5.4.0-42 linux-headers-5.4.0-42-generic linux-image-5.4.0-42-generic linux-modules-5.4.0-42-generic linux-modules-extra-5.4.0-42-generic Use 'sudo apt autoremove' to remove them. The following additional packages will be installed: ldap-utils libbasicobjects0 libc-ares2 libcollection4 libdhash1 libini-config5 libipa-hbac0 libnfsidmap2 libnss-sss libpam-pwquality libpam-sss libpath-utils1 libref-array1 libsasl2-modules-gssapi-mit libsss-certmap0 libsss-idmap0 libsss-nss-idmap0 libsss-sudo python3-sss sssd sssd-ad-common sssd-common sssd-ipa sssd-krb5 sssd-krb5-common sssd-ldap sssd-proxy Suggested packages: libsasl2-modules-ldap The following NEW packages will be installed: adcli ldap-utils libbasicobjects0 libc-ares2 libcollection4 libdhash1 libini-config5 libipa-hbac0 libnfsidmap2 libnss-sss libpam-pwquality libpam-sss libpath-utils1 libref-array1 libsasl2-modules-gssapi-mit libsss-certmap0 libsss-idmap0 libsss-nss-idmap0 libsss-sudo python3-sss realmd sssd sssd-ad sssd-ad-common sssd-common sssd-ipa sssd-krb5 sssd-krb5-common sssd-ldap sssd-proxy sssd-tools 0 upgraded, 31 newly installed, 0 to remove and 0 not upgraded. Need to get 2484 kB of archives. After this operation, 11.2 MB of additional disk space will be used. Do you want to continue? [Y/n] Y Get:1 http://jp.archive.ubuntu.com/ubuntu focal/main amd64 libsasl2-modules-gssapi-mit amd64 2.1.27+dfsg-2 [36.8 kB] (snip) Get:30 http://jp.archive.ubuntu.com/ubuntu focal-updates/main amd64 sssd amd64 2.2.3-3ubuntu0.8 [4232 B] Get:31 http://jp.archive.ubuntu.com/ubuntu focal-updates/main amd64 sssd-tools amd64 2.2.3-3ubuntu0.8 [94.7 kB] Fetched 2484 kB in 3s (971 kB/s) Extracting templates from packages: 100% Selecting previously unselected package libsasl2-modules-gssapi-mit:amd64. (Reading database ... 200337 files and directories currently installed.) Preparing to unpack .../00-libsasl2-modules-gssapi-mit_2.1.27+dfsg-2_amd64.deb ... Unpacking libsasl2-modules-gssapi-mit:amd64 (2.1.27+dfsg-2) ... Selecting previously unselected package adcli. Preparing to unpack .../01-adcli_0.9.0-1ubuntu0.20.04.1_amd64.deb ... Unpacking adcli (0.9.0-1ubuntu0.20.04.1) ... Selecting previously unselected package ldap-utils. Preparing to unpack .../02-ldap-utils_2.4.49+dfsg-2ubuntu1.8_amd64.deb ... Unpacking ldap-utils (2.4.49+dfsg-2ubuntu1.8) ... Selecting previously unselected package libnfsidmap2:amd64. Preparing to unpack .../03-libnfsidmap2_0.25-5.1ubuntu1_amd64.deb ... Unpacking libnfsidmap2:amd64 (0.25-5.1ubuntu1) ... Selecting previously unselected package libpam-pwquality:amd64. Preparing to unpack .../04-libpam-pwquality_1.4.2-1build1_amd64.deb ... Unpacking libpam-pwquality:amd64 (1.4.2-1build1) ... Selecting previously unselected package realmd. Preparing to unpack .../05-realmd_0.16.3-3_amd64.deb ... Unpacking realmd (0.16.3-3) ... Selecting previously unselected package libbasicobjects0:amd64. Preparing to unpack .../06-libbasicobjects0_0.6.1-2_amd64.deb ... Unpacking libbasicobjects0:amd64 (0.6.1-2) ... Selecting previously unselected package libc-ares2:amd64. Preparing to unpack .../07-libc-ares2_1.15.0-1ubuntu0.1_amd64.deb ... Unpacking libc-ares2:amd64 (1.15.0-1ubuntu0.1) ... Selecting previously unselected package libcollection4:amd64. Preparing to unpack .../08-libcollection4_0.6.1-2_amd64.deb ... Unpacking libcollection4:amd64 (0.6.1-2) ... Selecting previously unselected package libdhash1:amd64. Preparing to unpack .../09-libdhash1_0.6.1-2_amd64.deb ... Unpacking libdhash1:amd64 (0.6.1-2) ... Selecting previously unselected package libpath-utils1:amd64. Preparing to unpack .../10-libpath-utils1_0.6.1-2_amd64.deb ... Unpacking libpath-utils1:amd64 (0.6.1-2) ... Selecting previously unselected package libref-array1:amd64. Preparing to unpack .../11-libref-array1_0.6.1-2_amd64.deb ... Unpacking libref-array1:amd64 (0.6.1-2) ... Selecting previously unselected package libini-config5:amd64. Preparing to unpack .../12-libini-config5_0.6.1-2_amd64.deb ... Unpacking libini-config5:amd64 (0.6.1-2) ... Selecting previously unselected package libipa-hbac0. Preparing to unpack .../13-libipa-hbac0_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking libipa-hbac0 (2.2.3-3ubuntu0.8) ... Selecting previously unselected package libnss-sss:amd64. Preparing to unpack .../14-libnss-sss_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking libnss-sss:amd64 (2.2.3-3ubuntu0.8) ... Selecting previously unselected package libpam-sss:amd64. Preparing to unpack .../15-libpam-sss_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking libpam-sss:amd64 (2.2.3-3ubuntu0.8) ... Selecting previously unselected package libsss-certmap0. Preparing to unpack .../16-libsss-certmap0_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking libsss-certmap0 (2.2.3-3ubuntu0.8) ... Selecting previously unselected package libsss-idmap0. Preparing to unpack .../17-libsss-idmap0_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking libsss-idmap0 (2.2.3-3ubuntu0.8) ... Selecting previously unselected package libsss-nss-idmap0. Preparing to unpack .../18-libsss-nss-idmap0_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking libsss-nss-idmap0 (2.2.3-3ubuntu0.8) ... Selecting previously unselected package libsss-sudo. Preparing to unpack .../19-libsss-sudo_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking libsss-sudo (2.2.3-3ubuntu0.8) ... Selecting previously unselected package python3-sss. Preparing to unpack .../20-python3-sss_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking python3-sss (2.2.3-3ubuntu0.8) ... Selecting previously unselected package sssd-common. Preparing to unpack .../21-sssd-common_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking sssd-common (2.2.3-3ubuntu0.8) ... Selecting previously unselected package sssd-ad-common. Preparing to unpack .../22-sssd-ad-common_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking sssd-ad-common (2.2.3-3ubuntu0.8) ... Selecting previously unselected package sssd-krb5-common. Preparing to unpack .../23-sssd-krb5-common_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking sssd-krb5-common (2.2.3-3ubuntu0.8) ... Selecting previously unselected package sssd-ad. Preparing to unpack .../24-sssd-ad_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking sssd-ad (2.2.3-3ubuntu0.8) ... Selecting previously unselected package sssd-ipa. Preparing to unpack .../25-sssd-ipa_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking sssd-ipa (2.2.3-3ubuntu0.8) ... Selecting previously unselected package sssd-krb5. Preparing to unpack .../26-sssd-krb5_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking sssd-krb5 (2.2.3-3ubuntu0.8) ... Selecting previously unselected package sssd-ldap. Preparing to unpack .../27-sssd-ldap_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking sssd-ldap (2.2.3-3ubuntu0.8) ... Selecting previously unselected package sssd-proxy. Preparing to unpack .../28-sssd-proxy_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking sssd-proxy (2.2.3-3ubuntu0.8) ... Selecting previously unselected package sssd. Preparing to unpack .../29-sssd_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking sssd (2.2.3-3ubuntu0.8) ... Selecting previously unselected package sssd-tools. Preparing to unpack .../30-sssd-tools_2.2.3-3ubuntu0.8_amd64.deb ... Unpacking sssd-tools (2.2.3-3ubuntu0.8) ... Setting up libpath-utils1:amd64 (0.6.1-2) ... Setting up libsss-idmap0 (2.2.3-3ubuntu0.8) ... Setting up libbasicobjects0:amd64 (0.6.1-2) ... Setting up realmd (0.16.3-3) ... realmd.service is a disabled or a static unit, not starting it. Setting up libsss-sudo (2.2.3-3ubuntu0.8) ... Checking NSS setup... Setting up libpam-pwquality:amd64 (1.4.2-1build1) ... Setting up libc-ares2:amd64 (1.15.0-1ubuntu0.1) ... Setting up ldap-utils (2.4.49+dfsg-2ubuntu1.8) ... Setting up python3-sss (2.2.3-3ubuntu0.8) ... Setting up libsss-certmap0 (2.2.3-3ubuntu0.8) ... Setting up libdhash1:amd64 (0.6.1-2) ... Setting up libcollection4:amd64 (0.6.1-2) ... Setting up libipa-hbac0 (2.2.3-3ubuntu0.8) ... Setting up libref-array1:amd64 (0.6.1-2) ... Setting up libnfsidmap2:amd64 (0.25-5.1ubuntu1) ... Setting up libsss-nss-idmap0 (2.2.3-3ubuntu0.8) ... Setting up libsasl2-modules-gssapi-mit:amd64 (2.1.27+dfsg-2) ... Setting up libpam-sss:amd64 (2.2.3-3ubuntu0.8) ... Setting up libnss-sss:amd64 (2.2.3-3ubuntu0.8) ... First installation detected... Checking NSS setup... Adding an entry for automount. Setting up libini-config5:amd64 (0.6.1-2) ... Setting up adcli (0.9.0-1ubuntu0.20.04.1) ... Setting up sssd-common (2.2.3-3ubuntu0.8) ... Creating SSSD system user & group... adduser: Warning: The home directory `/var/lib/sss' does not belong to the user you are currently creating. Warning: found usr.sbin.sssd in /etc/apparmor.d/force-complain, forcing complain mode Warning from /etc/apparmor.d/usr.sbin.sssd (/etc/apparmor.d/usr.sbin.sssd line 59): Warning failed to create cache: usr.sbin.sssd Created symlink /etc/systemd/system/sssd.service.wants/sssd-autofs.socket -> /lib/systemd/system/sssd-autofs.socket. Created symlink /etc/systemd/system/sssd.service.wants/sssd-nss.socket -> /lib/systemd/system/sssd-nss.socket. Created symlink /etc/systemd/system/sssd.service.wants/sssd-pam-priv.socket -> /lib/systemd/system/sssd-pam-priv.socket. Created symlink /etc/systemd/system/sssd.service.wants/sssd-pam.socket -> /lib/systemd/system/sssd-pam.socket. Created symlink /etc/systemd/system/sssd.service.wants/sssd-ssh.socket -> /lib/systemd/system/sssd-ssh.socket. Created symlink /etc/systemd/system/sssd.service.wants/sssd-sudo.socket -> /lib/systemd/system/sssd-sudo.socket. Created symlink /etc/systemd/system/multi-user.target.wants/sssd.service -> /lib/systemd/system/sssd.service. sssd-autofs.service is a disabled or a static unit, not starting it. sssd-nss.service is a disabled or a static unit, not starting it. sssd-pam.service is a disabled or a static unit, not starting it. sssd-ssh.service is a disabled or a static unit, not starting it. sssd-sudo.service is a disabled or a static unit, not starting it. A dependency job for sssd-autofs.socket failed. See 'journalctl -xe' for details. A dependency job for sssd-nss.socket failed. See 'journalctl -xe' for details. A dependency job for sssd-pam-priv.socket failed. See 'journalctl -xe' for details. A dependency job for sssd-pam.socket failed. See 'journalctl -xe' for details. A dependency job for sssd-ssh.socket failed. See 'journalctl -xe' for details. A dependency job for sssd-sudo.socket failed. See 'journalctl -xe' for details. Setting up sssd-proxy (2.2.3-3ubuntu0.8) ... Setting up sssd-ad-common (2.2.3-3ubuntu0.8) ... Created symlink /etc/systemd/system/sssd.service.wants/sssd-pac.socket -> /lib/systemd/system/sssd-pac.socket. sssd-pac.service is a disabled or a static unit, not starting it. A dependency job for sssd-pac.socket failed. See 'journalctl -xe' for details. Setting up sssd-krb5-common (2.2.3-3ubuntu0.8) ... Setting up sssd-krb5 (2.2.3-3ubuntu0.8) ... Setting up sssd-ldap (2.2.3-3ubuntu0.8) ... Setting up sssd-ad (2.2.3-3ubuntu0.8) ... Setting up sssd-tools (2.2.3-3ubuntu0.8) ... Setting up sssd-ipa (2.2.3-3ubuntu0.8) ... Setting up sssd (2.2.3-3ubuntu0.8) ... Processing triggers for systemd (245.4-4ubuntu3.15) ... Processing triggers for man-db (2.9.1-1) ... Processing triggers for dbus (1.12.16-2ubuntu2.1) ... Processing triggers for libc-bin (2.31-0ubuntu9.2) ... |
今は/etc/resolv.confを編集してはダメなんですね。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
rootlinks@Ubuntu20:~$ cat /etc/resolv.conf # This file is managed by man:systemd-resolved(8). Do not edit. # # This is a dynamic resolv.conf file for connecting local clients to the # internal DNS stub resolver of systemd-resolved. This file lists all # configured search domains. # # Run "resolvectl status" to see details about the uplink DNS servers # currently in use. # # Third party programs must not access this file directly, but only through the # symlink at /etc/resolv.conf. To manage man:resolv.conf(5) in a different way, # replace this symlink by a static file or a different symlink. # # See man:systemd-resolved.service(8) for details about the supported modes of # operation for /etc/resolv.conf. nameserver 127.0.0.53 options edns0 trust-ad |
“resolvectl status“で現在の設定を確認できるようなので。
DNSがActive Directory DNSに設定されています。ここ重要です。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 |
rootlinks@Ubuntu20:~$ resolvectl status Global LLMNR setting: no MulticastDNS setting: no DNSOverTLS setting: no DNSSEC setting: no DNSSEC supported: no DNSSEC NTA: 10.in-addr.arpa 16.172.in-addr.arpa 168.192.in-addr.arpa 17.172.in-addr.arpa 18.172.in-addr.arpa 19.172.in-addr.arpa 20.172.in-addr.arpa 21.172.in-addr.arpa 22.172.in-addr.arpa 23.172.in-addr.arpa 24.172.in-addr.arpa 25.172.in-addr.arpa 26.172.in-addr.arpa 27.172.in-addr.arpa 28.172.in-addr.arpa 29.172.in-addr.arpa 30.172.in-addr.arpa 31.172.in-addr.arpa corp d.f.ip6.arpa home internal intranet lan local private test Link 2 (ens160) Current Scopes: DNS DefaultRoute setting: yes LLMNR setting: yes MulticastDNS setting: no DNSOverTLS setting: no DNSSEC setting: no DNSSEC supported: no Current DNS Server: 192.168.1.1 DNS Servers: 192.168.1.1 DNS Domain: ~. |
ドメインを見つけられました。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
rootlinks@Ubuntu20:~$ sudo realm -v discover win2019sv.example.jp * Resolving: _ldap._tcp.win2019sv.example.jp * Resolving: win2019sv.example.jp * Performing LDAP DSE lookup on: 192.168.1.1 * Successfully discovered: example.jp example.jp type: kerberos realm-name: EXAMPLE.JP domain-name: example.jp configured: no server-software: active-directory client-software: sssd required-package: sssd-tools required-package: sssd required-package: libnss-sss required-package: libpam-sss required-package: adcli required-package: samba-common-bin |
Active Directory管理者(administrator)のパスワードを入力します。-vオプションを付け忘れたので実にシンプルに(^^;
|
1 2 |
rootlinks@Ubuntu20:~$ sudo realm join win2019sv.example.jp Password for Administrator: |
デフォルトはadministratorですが、他のドメイン管理権限のあるユーザで実行する場合は-Uオプションを追加するとのことです。
Active Directoryにコンピュータアカウントが追加されました。
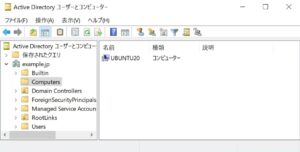
realm toolは必要なサービスの開始、pam, nssモジュールの追加、sssdの環境設定など全部やってますと。
拍子抜けするほど簡単ですね。
The realm tool already took care of creating an sssd configuration, adding the pam and nss modules, and starting the necessary services.
sssdの環境設定ファイルは/etc/sssd/sssd.confです。
ホームディレクトリの場所の記述がありますが、%uはユーザID, 5dはドメイン名になります。
デフォルトでは /home/user_id@example.jpがホームディレクトリになります。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
rootlinks@Ubuntu20:~$ sudo cat /etc/sssd/sssd.conf [sssd] domains = example.jp config_file_version = 2 services = nss, pam [domain/example.jp] default_shell = /bin/bash ad_server = win2019sv.example.jp krb5_store_password_if_offline = True cache_credentials = True krb5_realm = EXAMPLE.JP realmd_tags = manages-system joined-with-adcli id_provider = ad fallback_homedir = /home/%u@%d ad_domain = example.jp use_fully_qualified_names = True ldap_id_mapping = True access_provider = ad |
重要なことで/etc/sssd/sssd.confはオーナーroot:rootでパーミッションが0600になっていないとsssdが開始できないと。
Something very important to remember is that this file must have permissions 0600 and ownership root:root, or else sssd won’t start!
|
1 2 |
rootlinks@Ubuntu20:~$ ls -l /etc/sssd/sssd.conf -rw------- 1 root root 436 Jan 12 15:05 /etc/sssd/sssd.conf |
Let’s highlight a few things from this config:
cache_credentials: this allows logins when the AD server is unreachable
fallback_homedir: it’s by default /home/@ . For example, the AD user john will have a home directory of /home/john@ad1.example.com
use_fully_qualified_names: users will be of the form user@domain, not just user. This should only be changed if you are certain no other domains will ever join the AD forest, via one of the several possible trust relationships
いくつかの点を説明すると。
cache_credentialsはADに接続できない場合にキャッシュを使用してログインするか。
fallback_homedirはホームフォルダの場所と命名規則
use_fully_qualified_namesはuser_idだけでなくドメインも追加する(user@domain)。user_idだけにするなら、そのフォレストに他のドメインが追加しないことが大前提でよく考えて。
UbuntuのActive Directoryユーザでログインした時にホームディレクトリが無ければ自動で作成する設定です。
|
1 |
rootlinks@Ubuntu20:~$ sudo pam-auth-update --enable mkhomedir |
これは/etc/pam.d/common-sessionに1行追加されます。
|
1 |
session optional pam_mkhomedir.so |
|
1 2 |
rootlinks@Ubuntu20:~$ getent passwd guest01@example.jp guest01@example.jp:*:1734601105:1734601108:guest01:/home/guest01@example.jp:/bin/bash |
|
1 2 |
rootlinks@Ubuntu20:~$ groups guest01@example.jp guest01@example.jp : linuxgroup@example.jp domain users@example.jp |
ユーザーのグループメンバーシップを変更したばかりの場合は、キャッシュが原因でsssdが通知するまでにしばらく時間がかかることがあります。
Note
If you just changed the group membership of a user, it may be a while before sssd notices due to caching.
ADユーザのguest01でUbuntuにログインしてみます。
ログインIDにguest01@example.jpとすることに注意して下さい。これに気づかなくてuser_idだけでログインしようとしてずっと悩んでいました。
use_fully_qualified_names = FALSEに変更すればuser_idだけでログインできると思います。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
rootlinks@Ubuntu20:~$ sudo login Ubuntu20 login: guest01@example.jp Password: Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.11.0-43-generic x86_64) (snip) Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Creating directory '/home/guest01@example.jp'. guest01@example.jp@Ubuntu20:~$ pwd /home/guest01@example.jp guest01@example.jp@Ubuntu20:~$ id uid=1734601105(guest01@example.jp) gid=1734601108(linuxgroup@example.jp) groups=1734601108(linuxgroup@example.jp),1734600513(domain users@example.jp) guest01@example.jp@Ubuntu20:~$ whoami guest01@example.jp |
man realm
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 |
REALM(8) User Commands REALM(8) NAME realm - Manage enrollment in realms SYNOPSIS realm discover [realm-name] realm join [-U user] [realm-name] realm leave [-U user] [realm-name] realm list realm permit [-ax] [-R realm] {user@domain...} realm deny -a [-R realm] DESCRIPTION realm is a command line tool that can be used to manage enrollment in kerberos realms, like Active Directory domains or IPA domains. See the various sub commands below. The following global options can be used: --install=/path Run in install mode. This makes realmd chroot into the specified directory and place files in appropriate locations for use during an installer. No packages will be installed or services will be started when running in this mode. --unattended Run in unattended mode without prompting for input. --verbose, -v Display verbose diagnostics while doing running commands. DISCOVER Discover a realm and its capabilities. $ realm discover $ realm discover domain.example.com After discovering a realm, its name, type and capabilities are displayed. If no domain is specified, then the domain assigned through DHCP is used as a default. The following options can be used: --all Show all discovered realms (in various configurations). --client-software=xxx Only discover realms for which we can use the given client software. Possible values include sssd or winbind. --server-software=xxx Only discover realms which run the given server software. Possible values include active-directory or ipa. --membership-software=xxx Only discover realms for which the given membership software can be used to subsequently perform enrollment. Possible values include samba or adcli. JOIN Configure the local machine for use with a realm. $ realm join domain.example.com $ realm join --user=admin --computer-ou=OU=Special domain.example.com The realm is first discovered, as we would with the discover command. If no domain is specified, then the domain assigned through DHCP is used as a default. After a successful join, the computer will be in a state where it is able to resolve remote user and group names from the realm. For kerberos realms, a computer account and host keytab is created. Joining arbitrary kerberos realms is not supported. The realm must have a supported mechanism for joining from a client machine, such as Active Directory or IPA. If the domain has been preconfigured, and unless --user is explicitly specified, an automatic join is attempted first. Note that the --user, --no-password, and --one-time-password options are mutually exclusive. At most one of them can be specified. It is generally possible to use kerberos credentials to perform a join operation. Use the kinit command to acquire credentials prior to starting the join. Do not specify the --user argument, the user will be selected automatically from the credential cache. The realm respects the KRB5_CCACHE environment variable, but uses the default kerberos credential cache if it's not present. Not all types of servers can be joined using kerberos credentials, some (like IPA) insist on prompting for a password. The following options can be used: --automatic-id-mapping=no Do not perform UID/GID mapping for users and groups, but expect these identifiers to be present in the domain already. --user=xxx The user name to be used to authenticate with when joining the machine to the realm. You will be prompted for a password. --computer-ou=OU=xxx The distinguished name of an organizational unit to create the computer account. The exact format of the distinguished name depends on the client software and membership software. You can usually omit the root DSE portion of distinguished name. This is an Active Directory specific option. --no-password Perform the join automatically without a password. --one-time-password=xxxx Perform the join using a one time password specified on the command line. This is not possible with all types of realms. --client-software=xxx Only join realms for which we can use the given client software. Possible values include sssd or winbind. Not all values are supported for all realms. By default the client software is automatically selected. --server-software=xxx Only join realms for run the given server software. Possible values include active-directory or ipa. --membership-software=xxx The software to use when joining to the realm. Possible values include samba or adcli. Not all values are supported for all realms. By default the membership software is automatically selected. --user-principal=host/name@REALM Set the userPrincipalName field of the computer account to this kerberos principal. If you omit the value for this option, then a principal will be set in the form of host/shortname@REALM --os-name=xxx The name of the operation system of the client. When joining an AD domain the value is store in the matching AD attribute. --os-version=xxx The version of the operation system of the client. When joining an AD domain the value is store in the matching AD attribute. LEAVE Deconfigure the local machine for use with a realm. $ realm leave $ realm leave domain.example.com If no realm name is specified, then the first configured realm will be used. The following options can be used: --client-software=xxx Only leave the realm which is using the given client software. Possible values include sssd or winbind. --server-software=xxx Only leave the realm which is using the given server software. Possible values include active-directory or ipa. --remove Remove or disable computer account from the directory while leaving the realm. This will usually prompt for a pasword. --user The user name to be used to authenticate with when leaving the realm. You will be prompted for a password. Implies --remove. LIST List all the discovered and configured realms. $ realm list By default, realms that have been discovered, but not configured (using the join command), are not displayed. Also, by default, the list of realm details displayed is verbose. The options below can be used to change this default behavior The following options can be used: --all Show all discovered realms (whether or not they have been configured). --name-only Display only realm names (as opposed to verbose output). PERMIT Permit local login by users of the realm. $ realm permit --all $ realm permit user@example.com $ realm permit DOMAIN\\User2 $ realm permit --withdraw user@example.com The current login policy and format of the user names can be seen by using the realm list command. The following options can be used: --all, -a Permit logins using realm accounts on the local machine according to the realm policy.This usually defaults to allowing any realm user to log in. --groups, -g Treat the specified names as groups rather than user login names. Permit login by users in the specified groups. --realm, -R Specify the of the realm to change login policy for. --withdraw, -x Remove a login from the list of realm accounts permitted to log into the machine. DENY Deny local login by realm accounts. $ realm deny --all This command prevents realm accounts from logging into the local machine. Use realm permit to restrict logins to specific accounts. The following options can be used: --all, -a This option should be specified --realm, -R Specify the name of the realm to deny users login to. AUTHOR Stef Walter <stef@thewalter.net> Maintainer realmd 10/02/2019 REALM(8) |