MicrosoftがサポートしているOpenSSHをWindowsに移植するコミュニティのWin32-OpenSSHをインストールしてみました。
OpenSSH for Windowsリリース段階に到達 – Microsoft
http://news.mynavi.jp/news/2017/05/05/061/
OpenSSH for Windows Update
https://blogs.msdn.microsoft.com/powershell/2015/10/19/openssh-for-windows-update/
GitHub – PowerShell/Win32-OpenSSH: Win32 port of OpenSSH
https://github.com/PowerShell/Win32-OpenSSH
インストール環境
・Windows Server 2012 R2 評価版(Version 6.3.9600)
インストールについてはこちらの手順通りに行いました。
Install Win32 OpenSSH
https://github.com/PowerShell/Win32-OpenSSH/wiki/Install-Win32-OpenSSH
- ダウンロード
- 解凍と設置
- Powershellを管理者権限で実行
- OpenSSH directoryに移動
- インストール
- SSH host keysの作成
- Firewallの許可
- sshdサービスの自動起動設定
- sshdサービスの起動
- ファイルのアクセス権変更
- PATHの設定
プログラムをダウンロードします。
最新バージョンv0.0.21.0のOpenSSH-Win64.zipをダウンロードしました。
https://github.com/PowerShell/Win32-OpenSSH/releases
ダウンロードしたOpenSSH-Win64.zipを解凍して”C:\Program Files\OpenSSH”として設置します。
|
1 |
PS C:\Users\Administrator> cd 'C:\Program Files\OpenSSH' |
|
1 2 3 4 5 |
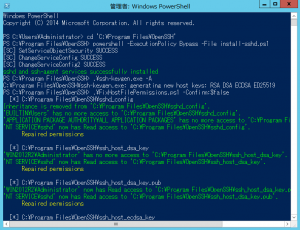
PS C:\Program Files\OpenSSH> powershell -ExecutionPolicy Bypass -File install-sshd.ps1 [SC] SetServiceObjectSecurity SUCCESS [SC] ChangeServiceConfig SUCCESS [SC] ChangeServiceConfig2 SUCCESS sshd and ssh-agent services successfully installed |
Windows 10で開発者モードを有効にしてWindows Subsystem for Linuxがインストール済みや、他のプログラムがポート22を使用していると競合が発生するので個別に対応が必要です。
|
1 2 |
PS C:\Program Files\OpenSSH> .\ssh-keygen.exe -A C:\Program Files\OpenSSH\ssh-keygen.exe: generating new host keys: RSA DSA ECDSA ED25519 |
Firewallでポート22を許可します。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
PS C:\Program Files\OpenSSH> New-NetFirewallRule -Protocol TCP -LocalPort 22 -Direction Inbound -Action Allow -DisplayName SSH Name : {8c1e8e92-fa41-4e4f-a734-8a02500d0f7e} DisplayName : SSH Description : DisplayGroup : Group : Enabled : True Profile : Any Platform : {} Direction : Inbound Action : Allow EdgeTraversalPolicy : Block LooseSourceMapping : False LocalOnlyMapping : False Owner : PrimaryStatus : OK Status : 規則は、ストアから正常に解析されました。 (65536) EnforcementStatus : NotApplicable PolicyStoreSource : PersistentStore PolicyStoreSourceType : Local |
|
1 |
PS C:\Program Files\OpenSSH> Set-Service sshd -StartupType Automatic |
|
1 2 3 |
PS C:\Program Files\OpenSSH> net start sshd sshd サービスを開始します. sshd サービスは正常に開始されました。 |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 |
PS C:\Program Files\OpenSSH> Powershell.exe -ExecutionPolicy Bypass -Command '. .\FixHostFilePermissions.ps1 -Confirm:$false' [*] C:\Program Files\OpenSSH\sshd_config Inheritance is removed from 'C:\Program Files\OpenSSH\sshd_config'. 'BUILTIN\Users' has no more access to 'C:\Program Files\OpenSSH\sshd_config'. 'APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES' has no more access to 'C:\Program Files\OpenSSH\sshd_config'. 'NT SERVICE\sshd' now has Read access to 'C:\Program Files\OpenSSH\sshd_config'. Repaired permissions [*] C:\Program Files\OpenSSH\ssh_host_dsa_key 'WIN2012R2\Administrator' has no more access to 'C:\Program Files\OpenSSH\ssh_host_dsa_key'. 'NT SERVICE\sshd' now has Read access to 'C:\Program Files\OpenSSH\ssh_host_dsa_key'. Repaired permissions [*] C:\Program Files\OpenSSH\ssh_host_dsa_key.pub 'WIN2012R2\Administrator' now has Read access to 'C:\Program Files\OpenSSH\ssh_host_dsa_key.pub'. 'NT SERVICE\sshd' now has Read access to 'C:\Program Files\OpenSSH\ssh_host_dsa_key.pub'. Repaired permissions [*] C:\Program Files\OpenSSH\ssh_host_ecdsa_key 'WIN2012R2\Administrator' has no more access to 'C:\Program Files\OpenSSH\ssh_host_ecdsa_key'. 'NT SERVICE\sshd' now has Read access to 'C:\Program Files\OpenSSH\ssh_host_ecdsa_key'. Repaired permissions [*] C:\Program Files\OpenSSH\ssh_host_ecdsa_key.pub 'WIN2012R2\Administrator' now has Read access to 'C:\Program Files\OpenSSH\ssh_host_ecdsa_key.pub'. 'NT SERVICE\sshd' now has Read access to 'C:\Program Files\OpenSSH\ssh_host_ecdsa_key.pub'. Repaired permissions [*] C:\Program Files\OpenSSH\ssh_host_ed25519_key 'WIN2012R2\Administrator' has no more access to 'C:\Program Files\OpenSSH\ssh_host_ed25519_key'. 'NT SERVICE\sshd' now has Read access to 'C:\Program Files\OpenSSH\ssh_host_ed25519_key'. Repaired permissions [*] C:\Program Files\OpenSSH\ssh_host_ed25519_key.pub 'WIN2012R2\Administrator' now has Read access to 'C:\Program Files\OpenSSH\ssh_host_ed25519_key.pub'. 'NT SERVICE\sshd' now has Read access to 'C:\Program Files\OpenSSH\ssh_host_ed25519_key.pub'. Repaired permissions [*] C:\Program Files\OpenSSH\ssh_host_rsa_key 'WIN2012R2\Administrator' has no more access to 'C:\Program Files\OpenSSH\ssh_host_rsa_key'. 'NT SERVICE\sshd' now has Read access to 'C:\Program Files\OpenSSH\ssh_host_rsa_key'. Repaired permissions [*] C:\Program Files\OpenSSH\ssh_host_rsa_key.pub 'WIN2012R2\Administrator' now has Read access to 'C:\Program Files\OpenSSH\ssh_host_rsa_key.pub'. 'NT SERVICE\sshd' now has Read access to 'C:\Program Files\OpenSSH\ssh_host_rsa_key.pub'. Repaired permissions Done. |
sshなどのコマンドを利用するならPATHの設定をする方がいいですね。
|
1 2 3 |
PS C:\Program Files\OpenSSH> setx PATH "%PATH%;C:\Program Files\OpenSSH" /M 成功: 指定した値は保存されました。 |
さて一通り設定できたのでTeraTermでadministratorでログインしてみます。
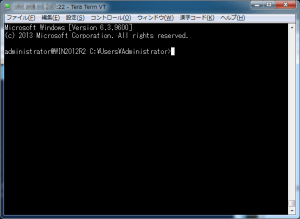
sshクライアントも利用できます。
|
1 2 3 4 5 6 7 8 |
C:\>ssh usage: ssh [-46AaCfGgKkMNnqsTtVvXxYy] [-b bind_address] [-c cipher_spec] [-D [bind_address:]port] [-E log_file] [-e escape_char] [-F configfile] [-I pkcs11] [-i identity_file] [-J [user@]host[:port]] [-L address] [-l login_name] [-m mac_spec] [-O ctl_cmd] [-o option] [-p port] [-Q query_option] [-R address] [-S ctl_path] [-W host:port] [-w local_tun[:remote_tun]] [user@]hostname [command] |
デフォルトのsshd設定(C:\Program Files\OpenSSH\sshd_config)ファイルです。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 |
# $OpenBSD: sshd_config,v 1.84 2011/05/23 03:30:07 djm Exp $ # This is the sshd server system-wide configuration file. See # sshd_config(5) for more information. # This sshd was compiled with PATH=/usr/bin:/bin:/usr/sbin:/sbin # The strategy used for options in the default sshd_config shipped with # OpenSSH is to specify options with their default value where # possible, but leave them commented. Uncommented options override the # default value. #Port 22 #AddressFamily any #ListenAddress 0.0.0.0 #ListenAddress :: # The default requires explicit activation of protocol 1 #Protocol 2 # HostKey for protocol version 1 #HostKey /etc/ssh/ssh_host_key # HostKeys for protocol version 2 #HostKey /etc/ssh/ssh_host_rsa_key #HostKey /etc/ssh/ssh_host_dsa_key #HostKey /etc/ssh/ssh_host_ecdsa_key # Lifetime and size of ephemeral version 1 server key #KeyRegenerationInterval 1h #ServerKeyBits 1024 # Logging # obsoletes QuietMode and FascistLogging #SyslogFacility AUTH #LogLevel INFO # Authentication: #LoginGraceTime 2m #PermitRootLogin yes #StrictModes yes #MaxAuthTries 6 #MaxSessions 10 #RSAAuthentication yes #PubkeyAuthentication yes # The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2 # but this is overridden so installations will only check .ssh/authorized_keys AuthorizedKeysFile .ssh/authorized_keys # For this to work you will also need host keys in /etc/ssh/ssh_known_hosts #RhostsRSAAuthentication no # similar for protocol version 2 #HostbasedAuthentication no # Change to yes if you don't trust ~/.ssh/known_hosts for # RhostsRSAAuthentication and HostbasedAuthentication #IgnoreUserKnownHosts no # Don't read the user's ~/.rhosts and ~/.shosts files #IgnoreRhosts yes # To disable tunneled clear text passwords, change to no here! #PasswordAuthentication yes #PermitEmptyPasswords no # Change to no to disable s/key passwords #ChallengeResponseAuthentication yes # Kerberos options #KerberosAuthentication no #KerberosOrLocalPasswd yes #KerberosTicketCleanup yes #KerberosGetAFSToken no # GSSAPI options #GSSAPIAuthentication no #GSSAPICleanupCredentials yes # Set this to 'yes' to enable PAM authentication, account processing, # and session processing. If this is enabled, PAM authentication will # be allowed through the ChallengeResponseAuthentication and # PasswordAuthentication. Depending on your PAM configuration, # PAM authentication via ChallengeResponseAuthentication may bypass # the setting of "PermitRootLogin without-password". # If you just want the PAM account and session checks to run without # PAM authentication, then enable this but set PasswordAuthentication # and ChallengeResponseAuthentication to 'no'. #UsePAM no #AllowAgentForwarding yes #AllowTcpForwarding yes #GatewayPorts no #X11Forwarding no #X11DisplayOffset 10 #X11UseLocalhost yes #PrintMotd yes #PrintLastLog yes #TCPKeepAlive yes #UseLogin no #UsePrivilegeSeparation yes #PermitUserEnvironment no #Compression delayed #ClientAliveInterval 0 #ClientAliveCountMax 3 #UseDNS yes #PidFile /var/run/sshd.pid #MaxStartups 10 #PermitTunnel no #ChrootDirectory none # no default banner path #Banner none # override default of no subsystems Subsystem sftp sftp-server.exe # Example of overriding settings on a per-user basis #Match User anoncvs # X11Forwarding no # AllowTcpForwarding no # ForceCommand cvs server # PubkeyAcceptedKeyTypes ssh-ed25519* hostkeyagent \\.\pipe\openssh-ssh-agent |