以前、SOCKS proxy serverのDanteをCentOS 7にインストールしました。
2年前ですね。
この時はrepositoryを見つけられなくてソース(dante-1.4.1.tar.gz)からインストールしました。
ちょっと気になって調べたらGhettoForge repositoryがDanteパッケージを提供しているようです。
dante-server-1.4.1-176.9.x86_64.rpm
https://centos.pkgs.org/7/ghettoforge-plus-x86_64/dante-server-1.4.1-176.9.x86_64.rpm.html
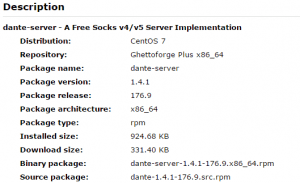
Install Howto
Download the latest gf-release rpm from
http://mirror.ghettoforge.org/distributions/gf/el/7/plus/x86_64/
Install gf-release rpm:
# rpm -Uvh gf-release*rpm
Install dante-server rpm package:
# yum –enablerepo=gf-plus install dante-server
試しにインストールしてみました。
- Install GhettoForge repository
- Install Dante server
- /etc/sockd.confの編集
- Firewallの許可
- サービスの有効化と開始
- logrotate
[gf]がデフォルトで有効になっています。[gf]は[base]/EPEL repoと競合しないパッケージの提供のようです。
List of Available Repositories & Suggested Usage
GhettoForge has multiple repositories that are organized as follows:
[gf] – This is the base repo that contains packages that do not conflict with packages in [base]/EPEL. This repo is enabled by default.
[gf-plus] – This repo is for packages that supercede or conflict with those in [base]/EPEL. This repo is disabled by default.
[gf-testing] – Packages that are not yet ready for production use are located in this repo. There is no distinction made here for packages which may conflict with those in [base]/EPEL. Users that are testing components are expected to understand that these packages may not be fully functional and that they may conflict. Caution is urged in using this repo. This repo is disabled by default.
[gf-source] – All source rpms for packages in the [gf] repo are located here.
[gf-plus-source] – Similarly source for packages in [gf-plus] can be found here.
[gf-testing-source] – Source for packages in [gf-testing] are here.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 |
# rpm -ivh http://mirror.ghettoforge.org/distributions/gf/gf-release-latest.gf.el7.noarch.rpm Retrieving http://mirror.ghettoforge.org/distributions/gf/gf-release-latest.gf.el7.noarch.rpm warning: /var/tmp/rpm-tmp.LIbyGX: Header V4 RSA/SHA1 Signature, key ID da8b7718: NOKEY Preparing... ################################# [100%] Updating / installing... 1:gf-release-7-10.gf.el7 ################################# [100%] # cat /etc/yum.repos.d/gf.repo [gf] name=Ghettoforge packages that won't overwrite core distro packages. mirrorlist=http://mirrorlist.ghettoforge.org/el/7/gf/$basearch/mirrorlist enabled=1 gpgcheck=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-gf.el7 failovermethod=priority [gf-plus] name=Ghettoforge packages that will overwrite core distro packages. mirrorlist=http://mirrorlist.ghettoforge.org/el/7/plus/$basearch/mirrorlist # Please read http://ghettoforge.org/index.php/Usage *before* enabling this repository! enabled=0 gpgcheck=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-gf.el7 failovermethod=priority (snip) |
Dante Serverは[gf-plus]にあります。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
# yum --enablerepo=gf-plus info dante-server Available Packages Name : dante-server Arch : x86_64 Version : 1.4.1 Release : 176.9 Size : 331 k Repo : gf-plus/x86_64 Summary : A Free Socks v4/v5 Server Implementation URL : http://www.inet.no/dante/ License : BSD-3-Clause Description : This package contains the socks proxy daemon and its documentation. The : sockd is the server part of the Dante socks proxy package and allows : socks clients to connect through it to the network. # repoquery --list --enablerepo=gf-plus dante-server /etc/sockd.conf /etc/tmpfiles.d/sockd.conf /usr/lib/systemd/system/sockd.service /usr/sbin/rcsockd /usr/sbin/sockd /usr/share/man/man5/sockd.conf.5.gz /usr/share/man/man8/sockd.8.gz |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 |
# yum --enablerepo=gf-plus install dante-server Resolving Dependencies --> Running transaction check ---> Package dante-server.x86_64 0:1.4.1-176.9 will be installed --> Processing Dependency: dante for package: dante-server-1.4.1-176.9.x86_64 --> Running transaction check ---> Package dante.x86_64 0:1.4.1-176.9 will be installed --> Finished Dependency Resolution Dependencies Resolved ============================================================================================================================================ Package Arch Version Repository Size ============================================================================================================================================ Installing: dante-server x86_64 1.4.1-176.9 gf-plus 331 k Installing for dependencies: dante x86_64 1.4.1-176.9 gf-plus 480 k Transaction Summary ============================================================================================================================================ Install 1 Package (+1 Dependent package) Total download size: 811 k Installed size: 2.4 M Is this ok [y/d/N]: y Downloading packages: warning: /var/cache/yum/x86_64/7/gf-plus/packages/dante-server-1.4.1-176.9.x86_64.rpm: Header V4 RSA/SHA1 Signature, key ID da8b7718: NOKEY Public key for dante-server-1.4.1-176.9.x86_64.rpm is not installed (1/2): dante-server-1.4.1-176.9.x86_64.rpm | 331 kB 00:00:02 (2/2): dante-1.4.1-176.9.x86_64.rpm | 480 kB 00:00:03 -------------------------------------------------------------------------------------------------------------------------------------------- Total 267 kB/s | 811 kB 00:00:03 Retrieving key from file:///etc/pki/rpm-gpg/RPM-GPG-KEY-gf.el7 Importing GPG key 0xDA8B7718: Userid : "Ghettoforge (el7) <gf@ghettoforge.org>" Fingerprint: b43e a892 86f4 b6fd ff83 fed1 d005 ae31 da8b 7718 Package : gf-release-7-10.gf.el7.noarch (installed) From : /etc/pki/rpm-gpg/RPM-GPG-KEY-gf.el7 Is this ok [y/N]: y Running transaction check Running transaction test Transaction test succeeded Running transaction Installing : dante-1.4.1-176.9.x86_64 1/2 Installing : dante-server-1.4.1-176.9.x86_64 2/2 Verifying : dante-server-1.4.1-176.9.x86_64 1/2 Verifying : dante-1.4.1-176.9.x86_64 2/2 Installed: dante-server.x86_64 0:1.4.1-176.9 Dependency Installed: dante.x86_64 0:1.4.1-176.9 Complete! |
許可するクライアント等を設定します。
[Default]
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 |
# $Id: sockd.conf,v 1.52.10.2 2014/09/03 14:49:13 michaels Exp $ # # A sample sockd.conf # # # The config file is divided into three parts; # 1) server settings # 2) rules # 3) routes # # The recommended order is: # Server settings: # logoutput # internal # external # socksmethod # clientmethod # users # compatibility # extension # timeout # srchost # # Rules: # client block/pass # from to # libwrap # log # # block/pass # from to # socksmethod # command # libwrap # log # protocol # proxyprotocol # # Routes: # the server will log both via syslog, to stdout and to /var/log/sockd.log #logoutput: syslog stdout /var/log/sockd.log logoutput: stderr # The server will bind to the address 10.1.1.1, port 1080 and will only # accept connections going to that address. #internal: 10.1.1.1 port = 1080 # Alternatively, the interface name can be used instead of the address. #internal: eth0 port = 1080 # all outgoing connections from the server will use the IP address # 195.168.1.1 #external: 192.168.1.1 # list over acceptable authentication methods, order of preference. # An authentication method not set here will never be selected. # # If the socksmethod field is not set in a rule, the global # socksmethod is filled in for that rule. # # methods for socks-rules. #socksmethod: username none #rfc931 # methods for client-rules. #clientmethod: none #or if you want to allow rfc931 (ident) too #socksmethod: username rfc931 none #or for PAM authentication #socksmethod: pam # # User identities, an important section. # # when doing something that can require privilege, it will use the # userid "sockd". #user.privileged: sockd # when running as usual, it will use the unprivileged userid of "sockd". #user.unprivileged: sockd # If you are not using libwrap, no need for the below line, so leave # it commented. # If you compiled with libwrap support, what userid should it use # when executing your libwrap commands? "libwrap". #user.libwrap: libwrap # # Some options to help clients with compatibility: # # when a client connection comes in the socks server will try to use # the same port as the client is using, when the socks server # goes out on the clients behalf (external: IP address). # If this option is set, Dante will try to do it for reserved ports as well. # This will usually require user.privileged to be set to "root". #compatibility: sameport # If you are using the Inferno Nettverk bind extension and have trouble # running servers via the server, you might try setting this. #compatibility: reuseaddr # # The Dante server supports some extensions to the socks protocol. # These require that the socks client implements the same extension and # can be enabled using the "extension" keyword. # # enable the bind extension. #extension: bind # # Misc options. # # how many seconds can pass from when a client connects til it has # sent us it's request? Adjust according to your network performance # and methods supported. #timeout.negotiate: 30 # on a lan, this should be enough. # how many seconds can the client and it's peer idle without sending # any data before we dump it? Unless you disable tcp keep-alive for # some reason, it's probably best to set this to 0, which is # "forever". #timeout.io: 0 # or perhaps 86400, for a day. # do you want to accept connections from addresses without # dns info? what about addresses having a mismatch in dns info? #srchost: nounknown nomismatch # # The actual rules. There are two kinds and they work at different levels. # # The rules prefixed with "client" are checked first and say who is allowed # and who is not allowed to speak/connect to the server. I.e the # ip range containing possibly valid clients. # It is especially important that these only use IP addresses, not hostnames, # for security reasons. # # The rules that do not have a "client" prefix are checked later, when the # client has sent its request and are used to evaluate the actual # request. # # The "to:" in the "client" context gives the address the connection # is accepted on, i.e the address the socks server is listening on, or # just "0.0.0.0/0" for any address the server is listening on. # # The "to:" in the non-"client" context gives the destination of the clients # socks request. # # "from:" is the source address in both contexts. # # # The "client" rules. All our clients come from the net 10.0.0.0/8. # # Allow our clients, also provides an example of the port range command. #client pass { # from: 10.0.0.0/8 port 1-65535 to: 0.0.0.0/0 # clientmethod: rfc931 # match all idented users that also are in passwordfile #} # This is identical to above, but allows clients without a rfc931 (ident) # too. In practice this means the socks server will try to get a rfc931 # reply first (the above rule), if that fails, it tries this rule. #client pass { # from: 10.0.0.0/8 port 1-65535 to: 0.0.0.0/0 #} # drop everyone else as soon as we can and log the connect, they are not # on our net and have no business connecting to us. This is the default # but if you give the rule yourself, you can specify details. #client block { # from: 0.0.0.0/0 to: 0.0.0.0/0 # log: connect error #} # the rules controlling what clients are allowed what requests # # you probably don't want people connecting to loopback addresses, # who knows what could happen then. #socks block { # from: 0.0.0.0/0 to: lo0 # log: connect error #} # the people at the 172.16.0.0/12 are bad, no one should talk to them. # log the connect request and also provide an example on how to # interact with libwrap. #socks block { # from: 0.0.0.0/0 to: 172.16.0.0/12 # libwrap: spawn finger @%a # log: connect error #} # unless you need it, you could block any bind requests. #socks block { # from: 0.0.0.0/0 to: 0.0.0.0/0 # command: bind # log: connect error #} # or you might want to allow it, for instance "active" ftp uses it. # Note that a "bindreply" command must also be allowed, it # should usually by from "0.0.0.0/0", i.e if a client of yours # has permission to bind, it will also have permission to accept # the reply from anywhere. #socks pass { # from: 10.0.0.0/8 to: 0.0.0.0/0 # command: bind # log: connect error #} # some connections expect some sort of "reply", this might be # the reply to a bind request or it may be the reply to a # udppacket, since udp is packet based. # Note that nothing is done to verify that it's a "genuine" reply, # that is in general not possible anyway. The below will allow # all "replies" in to your clients at the 10.0.0.0/8 net. #socks pass { # from: 0.0.0.0/0 to: 10.0.0.0/8 # command: bindreply udpreply # log: connect error #} # pass any http connects to the example.com domain if they # authenticate with username. # This matches "example.com" itself and everything ending in ".example.com". #socks pass { # from: 10.0.0.0/8 to: .example.com port = http # log: connect error # clientmethod: username #} # block any other http connects to the example.com domain. #socks block { # from: 0.0.0.0/0 to: .example.com port = http # log: connect error #} # everyone from our internal network, 10.0.0.0/8 is allowed to use # tcp and udp for everything else. #socks pass { # from: 10.0.0.0/8 to: 0.0.0.0/0 # protocol: tcp udp #} # last line, block everyone else. This is the default but if you provide # one yourself you can specify your own logging/actions #socks block { # from: 0.0.0.0/0 to: 0.0.0.0/0 # log: connect error #} # route all http connects via an upstream socks server, aka "server-chaining". #route { # from: 10.0.0.0/8 to: 0.0.0.0/0 port = http via: socks.example.net port = socks #} |
取り敢えず最小構成の設定ファイルを用意しました。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
logoutput: /var/log/sockd.log internal: eno16777736 port = 1080 external: eno16777736 socksmethod: none clientmethod: none client pass { from: 192.168.1.0/24 port 1-65535 to: 0.0.0.0/0 log: error connect disconnect } socks pass { from: 192.168.1.0/24 to: 0.0.0.0/0 protocol: tcp udp log: error connect disconnect } |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 |
# firewall-cmd --list-all public (active) target: default icmp-block-inversion: no interfaces: eno16777736 sources: services: dhcpv6-client ssh ports: protocols: masquerade: no forward-ports: sourceports: icmp-blocks: rich rules: # firewall-cmd --add-port=1080/tcp --permanent success # firewall-cmd --add-port=1080/udp --permanent success # firewall-cmd --reload success # firewall-cmd --list-all public (active) target: default icmp-block-inversion: no interfaces: eno16777736 sources: services: dhcpv6-client ssh ports: 1080/tcp 1080/udp protocols: masquerade: no forward-ports: sourceports: icmp-blocks: rich rules: |
エラーが表示されたら/etc/sockd.confを見直して下さい。
|
1 2 3 4 |
# systemctl enable sockd Created symlink from /etc/systemd/system/multi-user.target.wants/sockd.service to /usr/lib/systemd/system/sockd.service. # systemctl start sockd |
/etc/logrotate.d/sockdを作成します。
|
1 2 3 4 5 |
/var/log/sockd.log { missingok copytruncate notifempty } |
ブラウザのProxyを設定して表示できればdante経由で接続できています。
ログを確認するとセッションが記録されています。
|
1 2 |
Jun 20 11:12:30 (1498011150.966780) sockd[2938]: info: pass(1): tcp/connect ]: 1219 -> 192.168.1.2.53685 192.168.1.1.1080 -> 874, 874 -> 192.168.1.1.53685 183.79.215.137.443 -> 1219: local client error (Connection reset by peer). Session duration: 95s Jun 20 11:12:30 (1498011150.966801) sockd[2938]: info: pass(1): tcp/accept ]: 1219 -> 192.168.1.2.53685 192.168.1.1.1080 -> 874: local client error (Connection reset by peer). Session duration: 95s |
になみにこのDanteパッケージはlibwrapをサポートしていません。
|
1 2 |
# sockd -vv | grep build: build: gssapi mon-data mon-disconnect pam preload sess2 |