SSLv2の脆弱性攻撃 – DROWN Attackの確認方法です。
SSLの脆弱性で日本の大手サイトを含む全世界1100万以上のHTTPSサイトが攻撃を受け得ると判明
http://gigazine.net/news/20160302-drown-attack/
The DROWN Attack
https://drownattack.com/
DROWN check
https://drownattack.com/#check
ただこのチェックは収集された結果を表示するだけのようで、脆弱性サーバのリストに該当しなかったけど、こっちのミスかファイアウォールの中にいたかもしれないのでクライアント側でのプログラムでチェックするのをお勧めしますと。
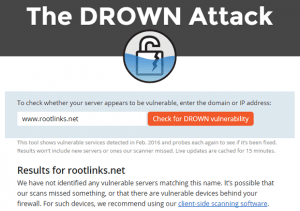
Results for rootlinks.net
We have not identified any vulnerable servers matching this name. It’s possible that our scans missed something, or that there are vulnerable devices behind your firewall. For such devices, we recommend using our client-side scanning software.
それならばとclient-side scanning softwareでチェックすることにしました。
DROWN Scanner
https://github.com/nimia/public_drown_scanner
実は発表直後にいろいろ試したのですがエラーで諦めてしまっていました。
CentOS:
Some users have encountered problems on CentOS with the asn1 package (or in general). In addition to installing the above dependencies for Fedora/RHEL, please see this issue for a suggested solution:
でも気になって再度調べたらそのものずばりの解説がありました。
OpenSSL の脆弱性 DROWN攻撃の対処と確認方法
http://s.webry.info/sp/vogel.at.webry.info/201603/article_2.html
この通りに作業を行えばOKでした。
結果だけですが。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
[root@host01 ~]# yum install python-enum scapy python-crypto tcpdump Loaded plugins: fastestmirror Loading mirror speeds from cached hostfile * base: ftp.iij.ad.jp * epel: ftp.iij.ad.jp * extras: ftp.iij.ad.jp * remi: remi.kazukioishi.net * updates: ftp.iij.ad.jp Package python-enum-0.4.4-9.el7.noarch already installed and latest version Package scapy-2.2.0-2.el7.noarch already installed and latest version Package python-crypto-2.6.1-1.el7.centos.x86_64 is obsoleted by python2-crypto-2.6.1-9.el7.x86_64 which is already installed Package 14:tcpdump-4.5.1-3.el7.x86_64 already installed and latest version Nothing to do |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 |
[root@host01 ~]# yum install python-virtualenv Loaded plugins: fastestmirror Loading mirror speeds from cached hostfile * base: ftp.iij.ad.jp * epel: ftp.iij.ad.jp * extras: ftp.iij.ad.jp * remi: remi.kazukioishi.net * updates: ftp.iij.ad.jp Resolving Dependencies --> Running transaction check ---> Package python-virtualenv.noarch 0:1.10.1-2.el7 will be installed --> Finished Dependency Resolution Dependencies Resolved ===================================================================================================== Package Arch Version Repository Size ===================================================================================================== Installing: python-virtualenv noarch 1.10.1-2.el7 base 1.2 M Transaction Summary ===================================================================================================== Install 1 Package Total download size: 1.2 M Installed size: 1.6 M Is this ok [y/d/N]: y Downloading packages: python-virtualenv-1.10.1-2.el7.noarch.rpm | 1.2 MB 00:00:00 Running transaction check Running transaction test Transaction test succeeded Running transaction Installing : python-virtualenv-1.10.1-2.el7.noarch 1/1 Verifying : python-virtualenv-1.10.1-2.el7.noarch 1/1 Installed: python-virtualenv.noarch 0:1.10.1-2.el7 Complete! |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
[matsuoka@host01 ~]# wget https://github.com/nimia/public_drown_scanner/archive/master.zip --2016-03-14 14:25:31-- https://github.com/nimia/public_drown_scanner/archive/master.zip Resolving github.com (github.com)... 192.30.252.130 Connecting to github.com (github.com)|192.30.252.130|:443... connected. HTTP request sent, awaiting response... 302 Found Location: https://codeload.github.com/nimia/public_drown_scanner/zip/master [following] --2016-03-14 14:25:32-- https://codeload.github.com/nimia/public_drown_scanner/zip/master Resolving codeload.github.com (codeload.github.com)... 192.30.252.162 Connecting to codeload.github.com (codeload.github.com)|192.30.252.162|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 71845 (70K) [application/zip] Saving to: 'master.zip' 100%[===========================================================>] 71,845 171KB/s in 0.4s 2016-03-14 14:25:34 (171 KB/s) - 'master.zip' saved [71845/71845] |
|
1 2 3 4 5 6 |
[matsuoka@host01 ~]# unzip master.zip Archive: master.zip 12a2c646f8b9fb1ca811e48f97afe424e5a9e75e creating: public_drown_scanner-master/ inflating: public_drown_scanner-master/.gitignore (snip) |
|
1 2 3 4 5 |
[matsuoka@host01 ~]# cd public_drown_scanner-master [matsuoka@host01 public_drown_scanner-master]# virtualenv drown New python executable in drown/bin/python Installing Setuptools..............................................................................................................................................................................................................................done. Installing Pip.....................................................................................................................................................................................................................................................................................................................................done. |
|
1 2 |
[matsuoka@host01 public_drown_scanner-master]# cd drown/ [matsuoka@host01 drown]# . ./bin/activate |
|
1 2 3 4 5 6 7 |
(drown)[matsuoka@host01 drown]# pip install enum pycrypto scapy pyasn1 scapy-ssl_tls Downloading/unpacking enum Downloading enum-0.4.6.tar.gz Running setup.py egg_info for package enum (snip) Successfully installed enum pycrypto scapy pyasn1 scapy-ssl-tls tinyec Cleaning up... |
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
(drown)[matsuoka@host01 drown]# python ../scanner.py localhost 443 Testing localhost on port 443 localhost: Case 3d; Server hello did not contain SSLv2 localhost: Server is NOT vulnerable with cipher RC2_128_CBC_EXPORT40_WITH_MD5, Message: 3d: no tls localhost: Case 3d; Server hello did not contain SSLv2 localhost: Server is NOT vulnerable with cipher RC4_128_EXPORT40_WITH_MD5, Message: 3d: no tls localhost: Case 3d; Server hello did not contain SSLv2 localhost: Server is NOT vulnerable with cipher RC4_128_WITH_MD5, Message: 3d: no tls localhost: Case 3d; Server hello did not contain SSLv2 localhost: Server is NOT vulnerable with cipher DES_64_CBC_WITH_MD5, Message: 3d: no tls |
|
1 2 |
(drown)[matsuoka@host01 drown]# deactivate [matsuoka@host01 drown]# |
取り敢えずOKでした。
ここに有名どころな脆弱性サイトのリストがあります。
Examples of Vulnerable Popular Sites
https://drownattack.com/top-sites.html
JPも24サイトありますが殆ど修正されているようです。ただ幾つかはまだそのままですね。