Meltdown (CVE-2017-5754) チェックプログラム – Am-I-affected-by-Meltdownを試してみました。
主要メーカー「CPU」に脆弱性、データ漏洩のおそれ – クラウド含む幅広い環境へ影響
http://www.security-next.com/088905
GitHub – raphaelsc/Am-I-affected-by-Meltdown
https://github.com/raphaelsc/Am-I-affected-by-Meltdown
環境はCentOS 7です。
- make
- Kernel 3.10.0-693.11.1.el7.x86_64
- yum update
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# git clone https://github.com/raphaelsc/Am-I-affected-by-Meltdown.git Cloning into 'Am-I-affected-by-Meltdown'... remote: Counting objects: 107, done. remote: Compressing objects: 100% (75/75), done. remote: Total 107 (delta 65), reused 73 (delta 32), pack-reused 0 Receiving objects: 100% (107/107), 101.70 KiB | 0 bytes/s, done. Resolving deltas: 100% (65/65), done. # cd Am-I-affected-by-Meltdown/ # make g++ -I. --std=c++11 -O0 --no-pie -mrtm -fPIC -c -o meltdown_checker.o meltdown_checker.cc g++ -I. --std=c++11 -O0 --no-pie -mrtm -fPIC -o meltdown-checker meltdown_checker.o |
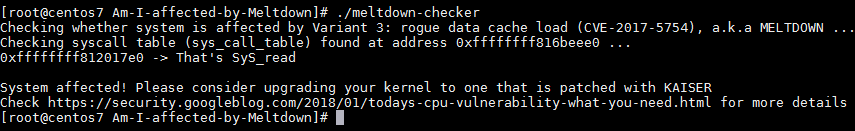
Kernel 3.10.0-693.11.1.el7.x86_64で実行してみます。
|
1 2 3 4 5 6 7 |
# ./meltdown-checker Checking whether system is affected by Variant 3: rogue data cache load (CVE-2017-5754), a.k.a MELTDOWN ... Checking syscall table (sys_call_table) found at address 0xffffffff816beee0 ... 0xffffffff812017e0 -> That's SyS_read System affected! Please consider upgrading your kernel to one that is patched with KAISER Check https://security.googleblog.com/2018/01/todays-cpu-vulnerability-what-you-need.html for more details |
System affected! Please consider upgrading your kernel to one that is patched with KAISER
脆弱性が存在しています。
yum updateですべてのpatchを適用、再起動します。
ちなみにKernel patchは1月4日にリリースされています。
[CentOS-announce] CESA-2018:0007 Important CentOS 7 kernel Security Update
https://lists.centos.org/pipermail/centos-announce/2018-January/022696.html
Kernel 3.10.0-693.11.6.el7.x86_64になりましたので同様にチェックしてみます。
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
# cd Am-I-affected-by-Meltdown/ # ./meltdown-checker Checking whether system is affected by Variant 3: rogue data cache load (CVE-2017-5754), a.k.a MELTDOWN ... Checking syscall table (sys_call_table) found at address 0xffffffff816c6ee0 ... 0x42e277d3ad02104c -> That's unknown 0x00124f1d5ea1ded5 -> That's unknown 0x721320031e2d066d -> That's unknown 0xa222093764440e0f -> That's unknown 0x01c1192c8aa91e0f -> That's unknown 0x47289524a0427a83 -> That's unknown 0x029430c7caa6520f -> That's unknown 0x363440315551e901 -> That's unknown 0x0001db6a0b1c2f10 -> That's unknown 0x1e47aa2b0c110007 -> That's unknown 0xac33063c2005cf1d -> That's unknown 0xa5d27a010107747a -> That's unknown 0x094938858c148103 -> That's unknown 0xcd29230b06261a8e -> That's unknown 0x0b154f082c3a1ce9 -> That's unknown 0x9d4e29e58a236e05 -> That's unknown |
24時間動作させましたがこの状態でした。
これは脆弱性無しと判断していいのかな?